NOTICE: This is a previous version of the Top 25. For the most recent version go here.
Introduction

Welcome to the 2022 Common Weakness Enumeration (CWE™) Top 25 Most Dangerous Software Weaknesses list (CWE™ Top 25). This list demonstrates the currently most common and impactful software weaknesses. Often easy to find and exploit, these can lead to exploitable vulnerabilities that allow adversaries to completely take over a system, steal data, or prevent applications from working.
Many professionals who deal with software will find the CWE Top 25 a practical and convenient resource to help mitigate risk. This may include software architects, designers, developers, testers, users, project managers, security researchers, educators, and contributors to standards developing organizations (SDOs).
To create the list, the CWE Team leveraged Common Vulnerabilities and Exposures (CVE™) data found within the National Institute of Standards and Technology (NIST) National Vulnerability Database (NVD) and the Common Vulnerability Scoring System (CVSS) scores associated with each CVE Record, including a focus on CVE Records from the Cybersecurity and Infrastructure Security Agency (CISA) Known Exploited Vulnerabilities (KEV) Catalog. A formula was applied to the data to score each weakness based on prevalence and severity.
The dataset analyzed to calculate the 2022 Top 25 contained a total of 37,899 CVE Records from the previous two calendar years.
Table of Contents
The CWE Top 25
Below is a list of the weaknesses in the 2022 CWE Top 25,
including the overall score of each. The KEV Count (CVEs) shows the number of CVE-2020/CVE-2021 Records from the CISA KEV list that were mapped to the given weakness.
| Rank | ID | Name | Score | KEV Count (CVEs) | Rank Change vs. 2021 |
|---|
| 1 | CWE-787 | Out-of-bounds Write | 64.20 | 62 | 0 |
| 2 | CWE-79 | Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') | 45.97 | 2 | 0 |
| 3 | CWE-89 | Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection') | 22.11 | 7 | +3  |
| 4 | CWE-20 | Improper Input Validation | 20.63 | 20 | 0 |
| 5 | CWE-125 | Out-of-bounds Read | 17.67 | 1 | -2  |
| 6 | CWE-78 | Improper Neutralization of Special Elements used in an OS Command ('OS Command Injection') | 17.53 | 32 | -1  |
| 7 | CWE-416 | Use After Free | 15.50 | 28 | 0 |
| 8 | CWE-22 | Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') | 14.08 | 19 | 0 |
| 9 | CWE-352 | Cross-Site Request Forgery (CSRF) | 11.53 | 1 | 0 |
| 10 | CWE-434 | Unrestricted Upload of File with Dangerous Type | 9.56 | 6 | 0 |
| 11 | CWE-476 | NULL Pointer Dereference | 7.15 | 0 | +4  |
| 12 | CWE-502 | Deserialization of Untrusted Data | 6.68 | 7 | +1 |
| 13 | CWE-190 | Integer Overflow or Wraparound | 6.53 | 2 | -1  |
| 14 | CWE-287 | Improper Authentication | 6.35 | 4 | 0 |
| 15 | CWE-798 | Use of Hard-coded Credentials | 5.66 | 0 | +1  |
| 16 | CWE-862 | Missing Authorization | 5.53 | 1 | +2  |
| 17 | CWE-77 | Improper Neutralization of Special Elements used in a Command ('Command Injection') | 5.42 | 5 | +8 |
| 18 | CWE-306 | Missing Authentication for Critical Function | 5.15 | 6 | -7 |
| 19 | CWE-119 | Improper Restriction of Operations within the Bounds of a Memory Buffer | 4.85 | 6 | -2 |
| 20 | CWE-276 | Incorrect Default Permissions | 4.84 | 0 | -1  |
| 21 | CWE-918 | Server-Side Request Forgery (SSRF) | 4.27 | 8 | +3  |
| 22 | CWE-362 | Concurrent Execution using Shared Resource with Improper Synchronization ('Race Condition') | 3.57 | 6 | +11  |
| 23 | CWE-400 | Uncontrolled Resource Consumption | 3.56 | 2 | +4  |
| 24 | CWE-611 | Improper Restriction of XML External Entity Reference | 3.38 | 0 | -1  |
| 25 | CWE-94 | Improper Control of Generation of Code ('Code Injection') | 3.32 | 4 | +3  |
Analysis and Comment
Key Points
There are several notable shifts in ranked positions of weakness types from last year's list, including several weaknesses dropping away or making their first appearance in a Top 25.
The biggest movers up the list are:
- CWE-362 (Concurrent Execution using Shared Resource with Improper Synchronization ('Race Condition')): from #33 to #22
- CWE-94 (Improper Control of Generation of Code ('Code Injection')): from #28 to #25
- CWE-400 (Uncontrolled Resource Consumption): from #27 to #23
- CWE-77 (Improper Neutralization of Special Elements used in a Command ('Command Injection')): from #25 to #17
- CWE-476 (NULL Pointer Dereference): from #15 to #11
The biggest downward movers are:
- CWE-306 (Missing Authentication for Critical Function): from #11 to #18
- CWE-200 (Exposure of Sensitive Information to an Unauthorized Actor): from #20 to #33
- CWE-522 (Insufficiently Protected Credentials): from #21 to #38
- CWE-732 (Incorrect Permission Assignment for Critical Resource): from #22 to #30
New entries in the Top 25 are:
- CWE-362 (Concurrent Execution using Shared Resource with Improper Synchronization ('Race Condition')): from #33 to #22
- CWE-94 (Improper Control of Generation of Code ('Code Injection')): from #28 to #25
- CWE-400 (Uncontrolled Resource Consumption): from #27 to #23
Entries that fell off the Top 25 are:
- CWE-200 (Exposure of Sensitive Information to an Unauthorized Actor): from #20 to #33
- CWE-522 (Insufficiently Protected Credentials): from #21 to #38
- CWE-732 (Incorrect Permission Assignment for Critical Resource): from #22 to #30
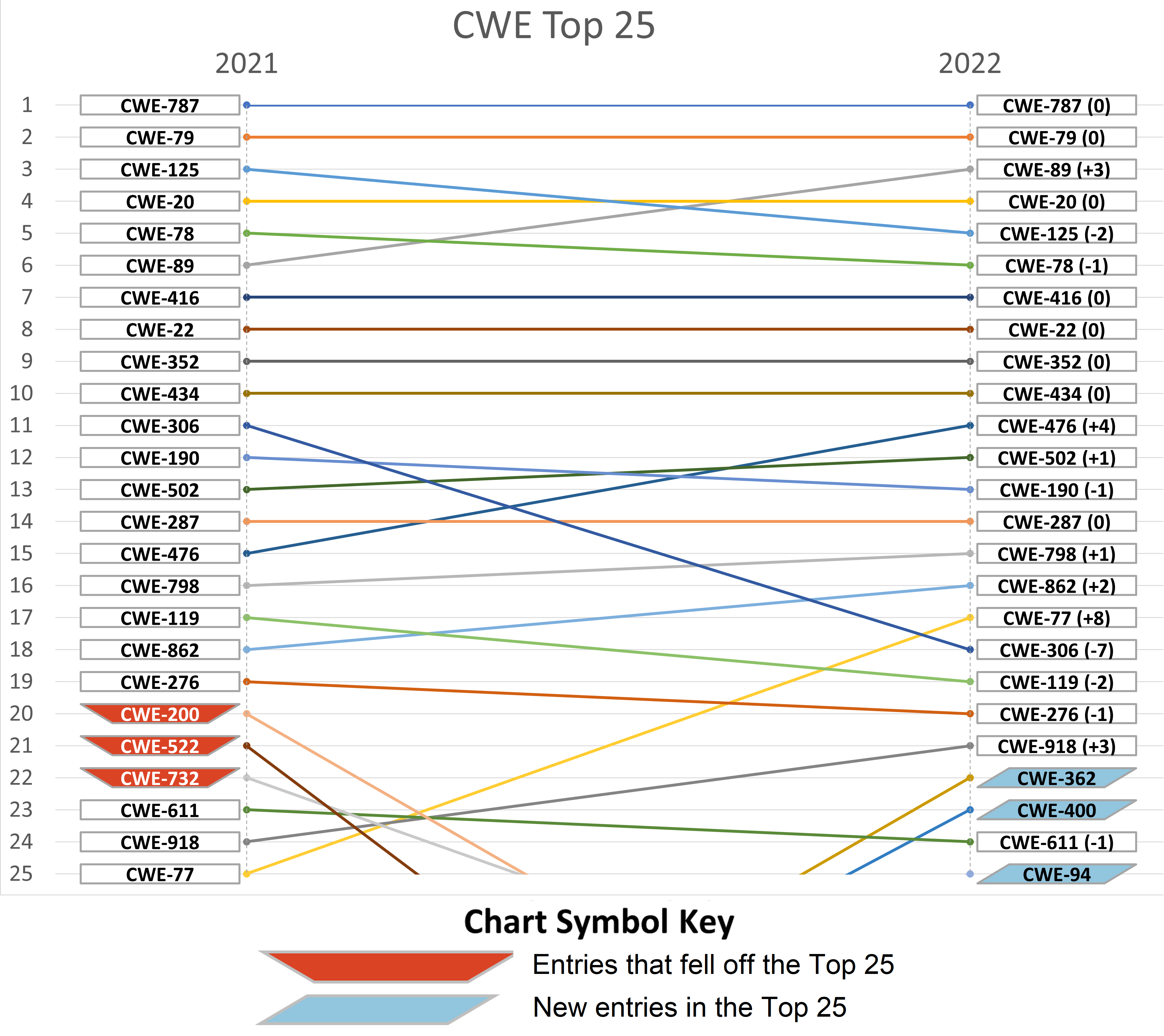
Below is a visual representation of the difference in 2021 and 2022 Top 25 lists.
General Insight
As with past years, there is a continued transition in the Top 25 to more specific Base-level weaknesses. While there is a slow decline in the number of unique Class-level weaknesses (from 9 in 2020 down to 7 in 2022), the percentage of all mappings used to generate the list has declined from 30% in 2020 down to 16% this year. Other levels for compound and variant weaknesses remain relatively unchanged. Data from 2019 is included for completeness, with 43% of all mappings going to classes, but this initial set of data had many categories, which is where the remapping analysis was focused; so, there was not as much extensive analysis of classes as in later years.
| Year | 2019 | % | 2020 | % | 2021 | % | 2022 | % |
|---|
| Unique Class/Pillar CWEs | 7 | 28% | 9 | 36% | 8 | 32% | 7 | 28% |
| Unique Base/Variant/Compound CWEs | 18 | 72% | 16 | 64% | 17 | 68% | 18 | 72% |
| Mappings to Class | 9548 | 43% | 6450 | 30% | 3058 | 17% | 3626 | 16% |
| Mappings to Base/Var/Comp | 12411 | 57% | 14772 | 70% | 14839 | 83% | 19254 | 84% |
| Total Maps with Top 25 CWEs | 21959 | | 21222 | | 17897 | | 22880 | |
| Maps to All CWEs | 26341 | | 27168 | | 24282 | | 30681 | |
| Maps to Bases | 10919 | 50% | 12988 | 61% | 13291 | 74% | 17386 | 76% |
| Maps to Variants | 799 | 4% | 918 | 4% | 807 | 5% | 1021 | 4% |
| Maps to Compounds | 693 | 3% | 866 | 4% | 741 | 4% | 847 | 4% |
While 7 class-level weaknesses still exist in the list, they
have declined noticeably in the ranking, as influenced by
prioritization in the remapping task (see Remapping Task). This
movement is expected to continue in future years as the community
improves its mappings to more precise weaknesses.
This year's analysis created a mixture of class and base-level weaknesses to move up and down from the Top 25. This is expected because some of these classes are generally well-known with easy to identifiable keywords such as 'race conditions', 'command injections', etc. The CWE Program's goal remains to iteratively provide more specificity through Base-level weakness types in the Top 25. As can be observed, each year gets closer to that goal. The program's goal is that this trend will benefit users attempting to better understand and address the issues that threaten today's systems at a more operational level, as Base-level weaknesses are more informative and conducive to practical mitigation than higher, Class-level weaknesses.
For those who are interested in why these shifts happened, see the "Remapping Task" section to learn how prioritization of remapping activities affected the rankings.
Methodology Overview
The 2022 CWE Top 25 was developed by obtaining and analyzing public vulnerability data from the NVD. For the 2022 list, data was used from the Known Exploited Vulnerabilities (KEV) Catalog, established in accordance with "Binding Operational Directive 22-01- Reducing the Significant Risk of Known Exploited Vulnerabilities" by CISA in November 2021. The KEV is an authoritative source of vulnerabilities that are known to have been exploited in the wild.
After the data collection and remapping process, a scoring formula was used to calculate a rank order of weaknesses that combines the frequency that a CWE is the root cause of a vulnerability with the average severity of each of those vulnerabilities exploitation as measured by CVSS. In both cases, the frequency and severity are normalized relative to the minimum and maximum values seen. In the next section, these metrics are presented as "NVD Count" and "Avg CVSS", respectively.
For more specific and detailed information on the calculation of
the 2022 Top 25 List, please see the Detailed Methodology.
The CWE Top 25 with Scoring Metrics
The following table shows the 2022 CWE Top 25 List with relevant scoring information, including the number of entries related to a particular CWE within the NVD data set, and the average CVSS score for each vulnerability mapped to a specific weakness.
Weaknesses On the Cusp
Per the scoring formula, these weaknesses were not severe enough or not prevalent enough to be included in the 2022 CWE Top 25.
Individuals who perform mitigation and risk decision-making using the 2022 CWE Top 25 List should consider including these additional weaknesses in their analyses because all weaknesses can become exploitable vulnerabilities under the right conditions:
| Rank | CWE | Name | NVD Count | Avg CVSS | Overall Score | KEV Count (CVEs) | Rank Change vs. 2021 |
|---|
| 26 | CWE-295 | Improper Certificate Validation | 242 | 6.95 | 3.12 | 2 | 0 |
| 27 | CWE-427 | Uncontrolled Search Path Element | 211 | 7.66 | 3.12 | 0 | +7  |
| 28 | CWE-863 | Incorrect Authorization | 250 | 6.76 | 3.10 | 0 | +10  |
| 29 | CWE-269 | Improper Privilege Management | 207 | 7.67 | 3.06 | 3 | 0 |
| 30 | CWE-732 | Incorrect Permission Assignment for Critical Resource | 212 | 7.31 | 2.93 | 1 | -8  |
| 31 | CWE-843 | Access of Resource Using Incompatible Type ('Type Confusion') | 173 | 8.34 | 2.87 | 10 | +5  |
| 32 | CWE-668 | Exposure of Resource to Wrong Sphere | 230 | 6.48 | 2.68 | 0 | +21  |
| 33 | CWE-200 | Exposure of Sensitive Information to an Unauthorized Actor | 241 | 5.99 | 2.49 | 2 | -13  |
| 34 | CWE-1321 | Improperly Controlled Modification of Object Prototype Attributes ('Prototype Pollution') | 140 | 8.77 | 2.48 | 0 | new |
| 35 | CWE-601 | URL Redirection to Untrusted Site ('Open Redirect') | 230 | 6.04 | 2.41 | 0 | +2  |
| 36 | CWE-401 | Missing Release of Memory after Effective Lifetime | 195 | 6.71 | 2.39 | 0 | -4  |
| 37 | CWE-59 | Improper Link Resolution Before File Access ('Link Following') | 183 | 7.00 | 2.38 | 4 | -6  |
| 38 | CWE-522 | Insufficiently Protected Credentials | 180 | 6.80 | 2.25 | 0 | -17  |
| 39 | CWE-319 | Cleartext Transmission of Sensitive Information | 174 | 6.74 | 2.15 | 0 | -4  |
| 40 | CWE-312 | Cleartext Storage of Sensitive Information | 182 | 6.25 | 2.01 | 0 | +1  |
These entries dropped from the Top 25 in 2021 to the 'On the Cusp' list in 2022:
- CWE-732 (Incorrect Permission Assignment for Critical Resource): from #22 to #30
- CWE-200 (Exposure of Sensitive Information to an Unauthorized Actor): from #20 to #33
- CWE-522 (Insufficiently Protected Credentials): from #21 to #38
These entries are newly 'On the Cusp' in 2022 :
- CWE-668 (Exposure of Resource to Wrong Sphere): from #53 to #32. It is not clear why such an increase has occurred since this is a class-level entry.
- CWE-312 (Cleartext Storage of Sensitive Information): from #41 to #40.
- CWE-1321 (Improperly Controlled Modification of Object Prototype Attributes ('Prototype Pollution')): new to list at #34. This entry was recently added to CWE and NVD View-1003, so it was not mapped in previous years.
These entries were 'On the Cusp' in 2021, but have dropped out in
2022:
- CWE-770 (Allocation of Resources Without Limits or Throttling): from #40 to #42
- CWE-532 (Insertion of Sensitive Information into Log File): from #39 to #49
- CWE-917 (Improper Neutralization of Special Elements used in an Expression Language Statement ('Expression Language Injection')): from #30 to #55
Remapping Task
To prepare the CVE/NVD data for analysis, the NVD entries were reviewed and the CWE mappings of these entries were "remapped" to the correct weakness, as appropriate. A "normalization" process converts selected weaknesses to the lowest-level CWE available in View-1003. For example, CWE-122: Heap-Based Buffer Overflow is not in View-1003, so it is "normalized" to its parent base-level weakness, CWE-787: Out-of-Bounds Write, which is in View-1003.
This year's remapping work was completed for 7,359 CVE Records in preparation for the 2022 Top 25 List. This year's analysis included CVE-2020-xxxx Records that had not been analyzed in 2021, as well as all CVE-2021-xxxx IDs that were published.
This year's remappingss were combined with 6,746 CVE-2020-xxxx remappings that had previously been done for 2021's Top 25, resulting in a total of 14,032 unique CVEs that were remapped across the last two years. This year's remapped data has been shared with NIST so that they can update their CVE Records within NVD.
The following is an overview of the process:
- Download a "snapshot" of NVD data from 2020 and 2021 and perform initial analysis. Snapshots were pulled several times in the ramp-up to the Top 25 publication, all of which introduced more CVE Records to analyze. In an attempt to start Top 25 remapping sooner than in previous years, the CWE Team obtained an initial snapshot on December 7, 2021 and used it for most remapping analyses until May. A final snapshot was downloaded on June 13, 2022 to generate the final Top 25 rankings. Any new CVEs found in the June 13, 2022 snapshot were not analyzed by the Top 25 team for consideration in the 2022 Top 25.
- As with previous years, for each NVD snapshot, a subset of all CVEs was automatically selected for remapping. Groups of approximately 50 CVEs were broken into "batches" that shared certain commonalities, e.g., buffer overflows, injection, or sources generally known to publish minimal details that are highly likely to produce an NVD entry with no mapping to the underlying CWE unless there is a reference from an independent third party. Top 25 Team members were assigned different batches based on their interest, relevant experience, expected complexity, and overall prioritization by team leads.
- In early rounds of remapping, batches were formed by performing automated keyword searches to suggest CVE Records that might have been incorrectly mapped. For example, some CVE Records were mapped to the higher-level CWE-119 (Improper Restriction of Operations within the Bounds of a Memory Buffer), but phrases related to 'out-of-bounds read' were automatically discoverable within their CVE descriptions. In those cases, mapping to the lower level CWE-125 (Out-of-bounds Read) is considered more appropriate. If a keyword match suggested a CWE ID that was already mapped within NVD, then the match was not reviewed.
- Extend the keyword matcher to detect potential mappings for many more CWE entries, including some that had only been created in the past year or two. In 2021, a related matcher was created to look for actual names of CWE entries within CVE descriptions; it was surprisingly successful in 2022 as well, indicating adoption of CWE-based names, whether intentional or not.
- Identify the highest-ranking classes based on a snapshot calculation of the Top 25 using the original NVD data from December 7, then investigate them more closely. There were six classes that appeared in an initial Top 25 calculation: CWE-20, CWE-269, CWE-200, CWE-284, CWE-119, and CWE-400. While four of these classes had already been seen in 2021, CWE-284 and CWE-400 were new. These "top 6" classes were added to a focus group and divided into batches.
- Choose additional subject areas for emphasis. This year's emphasis included access control, injection, cryptography/randomness, and remaining miscellaneous "high-level" classes that ranked from #26 to 50 in the snapshot (CWE-668 and CWE-755). Cryptography remaps had been investigated for the first time in 2021, so it seemed reasonable to reinvestigate for 2022. Access control was also targeted because of the prevalence of class-level access-control issues in the 2021 Top 25 and On the Cusp, as well as a suspicion that mappings would be inconsistent, which turned out to be true. Note: CWE-284 (the Pillar-level CWE for improper access control) had already been included in the focus group mentioned previously, so it was not part of this emphasis round. It should also be noted that CWE-362: Concurrent Execution using Shared Resource with Improper Synchronization ('Race Condition') - a child of the Pillar CWE-691: Insufficient Control Flow Management - was inadvertently omitted from this selection, although it ranked in the mid-30s in the initial snapshot.
- Perform deeper analysis in areas suspected to have mapping inaccuracies, especially injection (whose related weaknesses are many and full of nuance) and access control (for which terminology varies widely and often requires domain-specific knowledge to interpret). This typically involved looking more closely at references than in past years. For example, analysis in 2021 and earlier years showed that mappings to CWE-74 and CWE-77 had a good chance of being more precisely related to CWE-78 when analyzing references. (See CWE Top 25 Analysis). This pattern was also seen in 2022.
- Do not separately remap categories. There were few CVEs remaining that still mapped to categories, even though categories were eliminated from View-1003 in late 2019. CVEs mapped to categories were not analyzed as a group per se, but they were often included in other groups such as cryptography or keyword matches. It should be noted that some CNA sources still used categories in 2022 data.
- Improve the manual mapping process with automated tooling and annotations. While some of these improvements were experimental in 2021, they were fully adopted for 2022 and are likely to be used in future Top 25 lists. These improvements included automated syntax checks for manually-edited remapping reports provided by analysts; automated scraping of reference URLs for CWE IDs and keyword matches; and support for shifting CVE Records between different "analysis batches" to deprioritize or reassign CVEs that presented more complex analysis challenges.
- Create or enhance detailed mapping guidance for groups of related weaknesses and commonly-encountered mapping errors. These went into a greater level of detail than the publicly-available CWE Mapping Guidance. While useful for third-party analysts who perform CWE mapping for hundreds of CVEs, the guidance might be overkill for most CNAs.
- While the CWE team made every possible effort to minimize subjectivity in the remapping corrections, the lack of relevant, detailed information present in some CVE descriptions meant that a small portion of the dataset still required some subjective analytical conclusions.
In previous years, at the same time as the Top 25 release, the CWE-1003 view was also modified to ensure that it could still provide coverage for the most common CWE mappings. This created additional technical complexity for both NIST and the CWE Top 25 Team. In October 2021's release of CWE 4.6, View-1003 was updated to include CWE-1321, which was originally published in August 2020 and is a new entry to On the Cusp this year. However, View-1003 has not been updated for CWE 4.8. The CWE Team may update View-1003 for the CWE 4.9 release in Fall 2022.
Significant Changes to the Remapping Task in 2022
The Top 25 Team made several significant changes to the remapping task for 2022:
- Integrating CVMAP data from NVD into mapping analysis. NVD's CVMAP program allows CVE Numbering Authorities (CNAs) to submit their own CWE mappings for CVE Records within their purview. Top 25 analysts integrated these mappings as additional data points for remapping. CNA mappings were chosen in cases where there was insufficient detail to perform deeper analysis. This likely reduced the number of CVEs mapped to NVD-CWE-noinfo and gave some insight into possible mapping errors by the CNAs themselves. It also revealed over-use of some weaknesses such as CWE-20 and CWE-200.
- Analysts could represent chaining relationships between CWEs within a single vulnerability. A simple syntax was used: X->Y implied that weakness X triggered weakness Y. Longer chains were supported, e.g., X->Y->Z. In some cases, multiple chains existed within the same CVE Record. While the chaining representation did not influence the scoring this year, it provided valuable insights and real-world examples for how chains could be represented for vulnerabilities in the future. The Top 25 Team intends to share experiences with interested parties, including NIST.
- Due to the volume of potential CVEs to analyze, a process was defined to de-prioritize CVEs that were too complex and time-consuming to analyze. For example, a CVE could be related to an access control issue in an open-source product with a bug report containing dozens of product-specific comments trying to determine the right policy, or a voluminous diff report containing numerous changes besides fixes for the weakness. These complex CVEs were labeled "TODO" and were later resolved by experienced analysts or delayed for potential re-analysis next year. 219 CVEs were not resolved, i.e., they were too complex and time-consuming to choose an accurate remapping. Near the end of the remapping period, de-prioritization was also applied to CVEs that did not seem likely to affect final Top 25 results in any significant way; for example, many CVEs were de-prioritized if they mapped to CWE-20, due to the mathematical unlikelihood of CWE-20's rank to be changed; similarly, CWE-787 was so far ahead at #1, many of the associated CVEs were also de-prioritized. Therefore the scores for CWE-20 and CWE-787 might not be as accurate as the other scores. A total of 1,013 CVEs were not remapped or analyzed at all. This de-prioritization allowed analysts to focus on finishing CVEs with greater benefit to NVD / CNA analysts (to provide feedback on possible mapping errors), as well as analyzing CWEs near the bottom of the Top 25 or near the top of the On the Cusp, since even small shifts in rank could occur. For example, the CWE Team had more time to analyze cryptography-related issues as well as the CISA KEV list.
Remapping the CISA KEV Catalog
The Top 25 team downloaded KEV data on June 4, 2022. There were 280 total CVE Records with CVE-2020-nnnn or CVE-2021-nnnn IDs. Some had already been remapped as part of the 2021 Top 25 effort because they were for CVE-2020-nnnn Records. This year, the Top 25 team remapped the remainder of those KEV records including CVEs with keyword matches that were already consistent with NVD's own mappings. 10 CVEs were not fully remapped (mostly due to unresolved TODOs), so they inherited the original NVD mappings for the analysis.
The 270 remaps for this data set were then analyzed.
- 53 CVEs (20%) did not have sufficient details to conduct a remapping analysis, i.e., they were mapped to NVD-CWE-noinfo. This may be unexpected, since actively exploited vulnerabilities are often assumed to have significant public details.
- A custom Top-N list was created using Top 25 methodology, but only drawing from this limited set of 270 CVEs. This produced 47 unique CWEs. In terms of prevalence, only 14 CWEs were seen in 5 or more of the CVE Records. The rankings in the KEV list differed widely from the overall list. The Top 5 were CWE-787, CWE-78, CWE-416, CWE-20, and CWE-22 in that order. CWE-843 (Type Confusion) was ranked #6, compared to rank 31 for the overall list; however, this is not necessarily surprising, given type confusion's role in active exploitation of memory safety issues. On the other hand, only two instances of CWE-79 (XSS) were seen within the selected KEV set, leaving it at rank #30, compared to rank #2 on the overall list; similarly, CSRF (CWE-352) ranks #9 overall but was only reported for one CVE in KEV. CWE-125, which is #5 on the main list, only had 1 CVE Record in the KEV (rank #45). Finally, CWE-20 somehow kept the same #4 rank, being listed in 20 CVEs.
- 5 CWEs from the original Top 25 fell below rank 25 on the KEV list. 4 CWEs did not have any associated CVEs at all (CWE-276, CWE-476, CWE-611, and CWE-798).
Limitations of the Remapping Task
After using this remapping methodology for the Top 25 lists from 2019 through 2022, some limitations have become apparent:
- The number of CVEs with high-level CWE entries remains high, forcing manual remapping of many CVEs, which is labor-intensive.
- When remapping is performed over a short time frame before publication of the list, this increases timing and staffing pressures on Top 25 analysts during this period. Data exchange with NIST was improved to provide mapping data monthly over the entire review period, instead of all at once at the end. Still, the short time frame made it difficult for NVD staff to receive, analyze, and process all the mapping changes that required manual modifications as part of the CVMAP effort.
- Since data is from previous years, it prevents being able to give timely feedback to NIST staff and to CNAs so that they can adjust their training and mapping practices. However, due to regular check-ins, the NIST NVD and CWE Top 25 teams have been able to produce and tweak the guidance necessary to ensure future mappings will be more robust.
- The lack of relevant details for many CVEs continues to introduce time-consuming analysis and variability in mapping results, combined with increasing preference to analyze references more closely.
- Even within the CWE Top 25 Team itself, different analysts can be inconsistent in which CWE mappings they choose for the same CVE, especially for vulnerabilities that do not have very clear phrasing about the weakness. It is not clear whether this is a limitation of CWE itself, variations in terminology within CVE descriptions, analysts' varying perspectives and experience, or a combination of all these factors.
In the future, the remapping task might be changed to eliminate or mitigate these limitations.
Problematic CWEs Used in Mappings
Over the years, remapping by the CWE Team has revealed commonly cited CWEs that are either inappropriate, or not informative due to lack of sufficient details. These "problematic" CWEs make it difficult to tell from a large scale when some weaknesses are reduced as more-rare weaknesses arise. These problematic CWEs can have a significant impact on rankings within the Top 25 or any other CWE-based list.
While the Top 25 Team has not performed a formal data analysis on the most misused CWEs as revealed by remapping, the following CWEs are especially problematic:
- CWE-200: Exposure of Sensitive Information to an Unauthorized Actor
- CWE-269: Improper Privilege Management
- CWE-732: Incorrect Permission Assignment for Critical Resource
- CWE-77: Improper Neutralization of Special Elements used in a Command ('Command Injection')
- CWE-284: Improper Access Control
- CWE-668: Exposure of Resource to Wrong Sphere
- CWE-20: Improper Input Validation
- Categories
- Pillars and High-Level Classes
For more detailed information, please see the Details of Problematic Mappings section in the supplemental web page.
Trends Year-over-Year: 2019 to 2022 Lists
Graphs of trends in Top 25 rankings are presented. Note that these include data from CVE-2017-xxxx to CVE-2021-xxxx (due to the 2-year sliding window for each annual Top 25 list.)
- Some drops happen because of changes to View-1003 and/or more focused analysis. For example, in 2019, the Top 25 Team spent a lot of time on handling mappings to categories, and therefore did not look at all classes.
- As seen in the trends chart over the last four years, re-mapping analysis is providing good value in discovering more granular mappings. In partnership with the NIST NVD Analysis Team as well as the CNA and vendor community, the CWE Team's goal is to get to base-level weaknesses, improvements for which can be seen in this year's list.
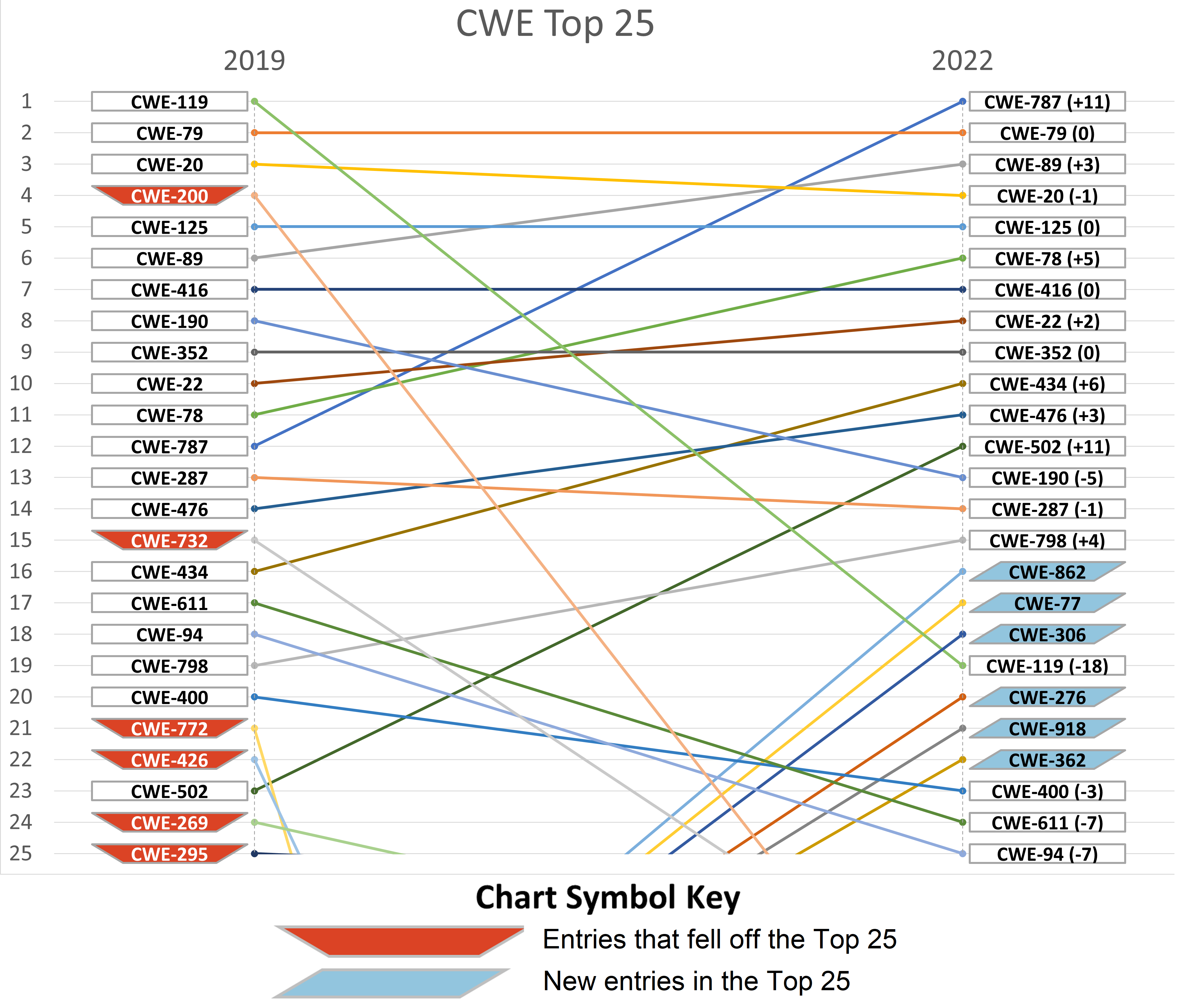
The first trend chart shows the significant changes from the 2019 Top 25 to the 2022 Top 25. Drops in high-level classes such as CWE-119 and CWE-200 are steep, while the shift and increase to Base-level weaknesses is most apparent for weaknesses such as CWE-787 and CWE-502.
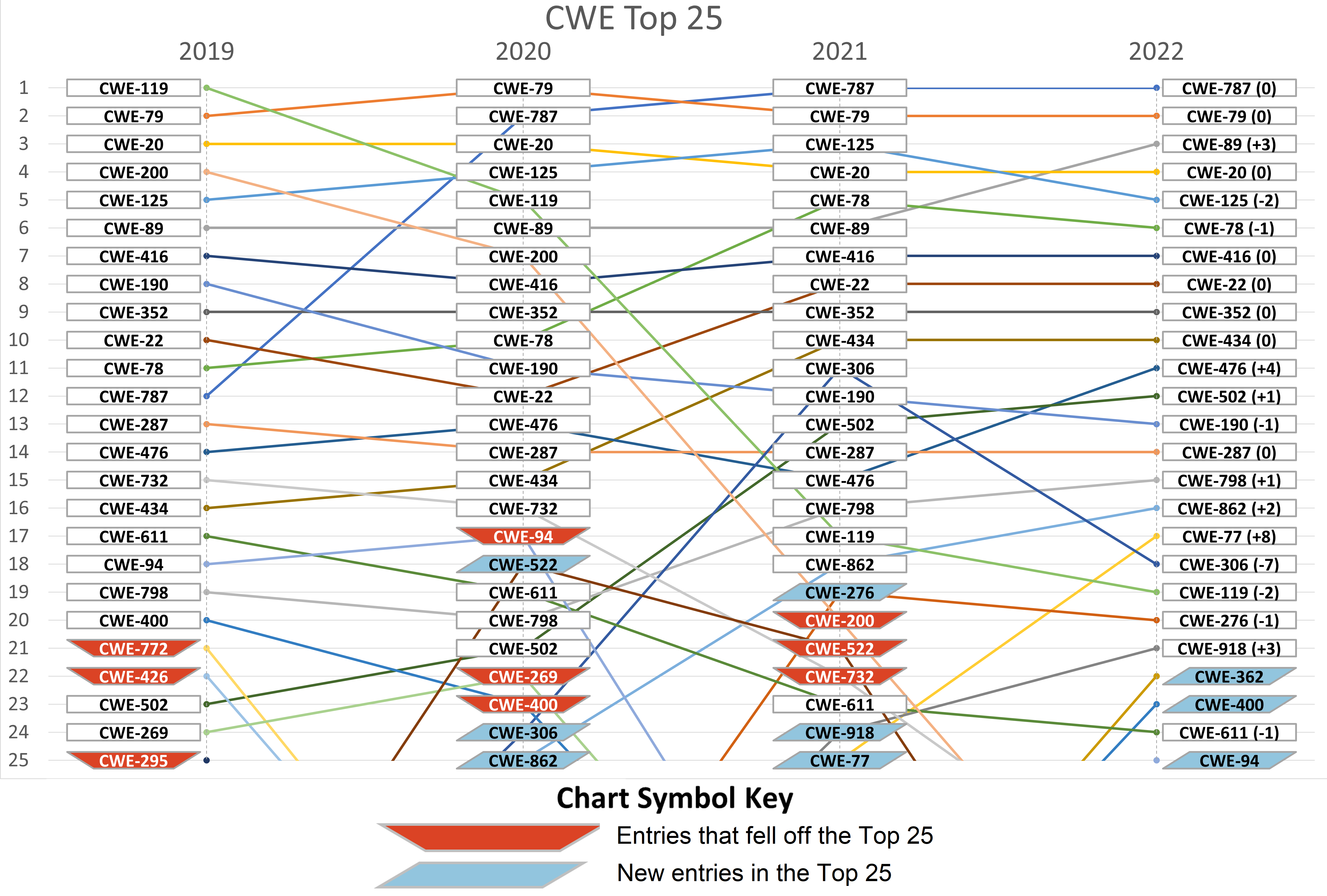
A second chart shows year-over-year changes from 2019 to 2022. One can see the relative stability in the top 10 from 2021 to 2022, along with the steady rise of CWE-502: "Deserialization of Untrusted Data" over all four years.
Opportunities for the Future of the Top 25
CWE is thrilled to share the 2022 Top 25 Most Dangerous Software
Weaknesses with the community, and the team hopes the list,
methodology, and supplemental information provides insight, value, and
utility. For those interested in learning more about where the CWE
team sees emerging opportunities and possibilities for future Top 25
lists, please visit the following sections on the
Supplementary
Details Page:
Supplementary Details - Methodology, Replication, Improving Mappings, Future
For additional technical and process details regarding this work, please visit the
Supplementary Details Page.
Summary of topics:
Acknowledgments
The 2022 CWE Top 25 Team includes (in alphabetical order): Alec Summers, Cathleen Zhang, Connor Mullaly, David Rothenberg, Jim Barry Jr., Kelly Todd, Luke Malinowski, Robert L. Heinemann, Jr., Rushi Purohit, Steve Christey Coley, and Trent DeLor. Members of the NIST NVD Analysis Team that coordinated on the Top 25 include Aleena Deen, Christopher Turner, David Jung, Robert Byers, Tanya Brewer, Tim Pinelli, and Vidya Ananthakrishna. Finally, thanks also to the broader CWE community for suggesting improvements to the process.
Archive
Past versions of the CWE Top 25 are available in the Archive.



